What is a Hardware Security Module (HSM)?

A hardware security module (HSM) is a trusted physical computing device that performs a variety of cryptographic operations, such as signing, signature validation, encryption, decryption and hashing. Hardware Security Modules typically come in the form of a physical appliance utilising specialised hardware and Operating Systems (OS) connected directly to the network. USB or PCI connected modules are another option for HSMs and are installed in network connected computers. Whilst these modules provide much the same functionality as physical appliances; they do not benefit from the security features of the hardened OS and with this deployment type the host machine is a critical component in the security chain. Hardware security modules should always be placed in a trusted environment; where there are controls and mechanisms deployed to ensure that it is in a known state. Possible controls would include anti-virus, anti-malware, strict access control limiting users who can access the environment and logging of all activity within the environment.

(Example of a PCIe HSM – Image Courtesy of Thales)
A Hardware Security Module is itself considered a trusted device because it is:
- Built on specialised hardware with tamper protections features
- Utilises a Hardened Operating System specifically designed or modified for the purpose of performing cryptographic functions
- certified by industry bodies to meet or exceed certain cryptographic security standards such as FIPS 140-2

(Example of a HSM Appliance – Image Courtesy of Thales)
Why Use a Hardware Security Module?
There are many reasons to utilise a HSM for your cryptographic functions. Some of these are listed below:
HSM Design – Tamper Resistance
Many HSMs have features that provide tamper resistance which make tampering difficult without making the device inoperable, or tamper responsiveness such as deleting keys upon tamper detection. Most also provide features to alert operators to potential tampering and provide evidence such as logging and alerting. In some cases the HSMs also provide direct physical indications of tampering on the device themselves.
HSM Design – Performance
HSMs are designed to perform a relatively small number of computing operations. But are specifically designed to perform them extremely efficiently and are highly optimised to undertake these specific operations. These optimisations mean that whilst commodity compute hardware can perform many thousands of cryptographic operations per second; a HSM can achieve numbers in the millions of operations per second.
HSM Design – High Availability
HSMs are commonly used for real time mission critical applications such as authorisation and authentication and are inherently designed with high-availability operation in mind. Typical high-availability features are redundant hot-swap modules like power supplies, appliance clustering with automated failover and seamless software upgrades.
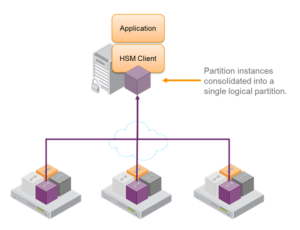
(HSM in a HA group – Image courtesy of Thales)
HSM Design – Security
Due to their nature HSMs are often utilised in securing critical infrastructure and applications ranging from banking applications to on-vehicle hardware. As such HSMs or the cryptographic modules utilised are often certified to international standards such as Common Criteria or FIPS 140 to provide independent verification that the design and implementation of the product offering is robust. These verifications are of critical importance when the HSMs are used within financial applications involving payments or payment process where the HSMs and its security will be validated against PCI-DSS standards.
HSM Design – Partitions
Some HSM vendors offer the ability to separate or partition a single physical HSM into multiple logical HSMs. These HSM partitions operate completely independently with regards to data storage, access controls and admin policies. Using partitions allows multiple applications to share the resources and security benefits offered by a HSM. Ensuring that one application cannot compromise another and providing each application with fine granularity admin controls that are applicable to its function.
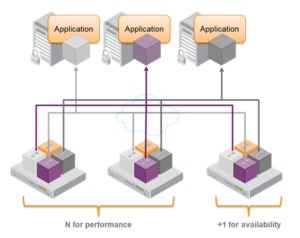
(HSM clustered for performance and availability utilising partitions – Image courtesy of Thales)
Some of the main functions of a HSM are:
- secure cryptographic key generation and storage
- key management
- cryptographic operations such as encryption/decryption using asymmetric or symmetric keys
- offloading cryptography functions from application servers
- managing encryption keys used by databases and other applications
- dedicated cryptographic accelerators and support for elliptic curve cryptography(ECC)
- specialised hardware providing excellent entropy
Use Cases for Hardware Security Modules
Hardware Security Modules should be used in any instance where digital keys are in use. These should be considered high value and stored using a system where they receive the maximum possible protection. The impact of digital keys being compromised is significant and the potential negative impact to the client, there customers and the overall damage to reputation justifies the relatively low cost of using HSMs.
Some common applications where digital keys are in use are outlined below:
Software Code Signing
Software Code Signing service the software end users or the systems on which the software is installed to verify that software images and updates are from a legitimate source. Our Software Code Signing service is utilised by premium automotive manufacturers to verify the software that is deployed to numerous vehicle Electronic Control Units (ECU). We utilise HSMs to offload the cryptographic operations used within our service and to store the digital key material.
Public Key Infrastructure (PKI)
In a PKI environment a Hardware Security Module is commonly used to create, store and managed the Asymmetric Key pairs that are used by the Certification and Registration authorities.
Card Payment Processing
Hardware Security Modules are widely used in the payment card industry driven by the need for high security and backed up by the requirements of standards such as PCI-DSS. The HSMs are often used for functions such as the authorisation of transactions and card personalisation. The HSM supports these functions with features such as PIN verification, PVV or CVV data creation and verification of card security codes during a transaction.
Payment authentication & PSD2
In January 2018 the EU introduced the second payment services directive known as PSD2. PSD2 introduces stricter requirements for authenticating online payments with effect from September 2019. These requirements known as Strong Customer Authentication (SCA) will introduce major changes to how users are authenticated and will involve using two of three methods of authentication. The introduction of these requirements will require the secure storage of biometric and other data utilised for authentication. This is an ideal use-case for a HSM for managing cryptographic keys.
Secure Sockets Layer Connection Establishment
When processing large numbers of SSL connections host CPU utilisation can become an issue where performance is critical. The RSA operations used in SSL are CPU intensive as they require a number of large multiplication operations. To address these potential performance bottlenecks these operations can be offloaded to a HSM.
Domain Name System Security Extensions (DNSSEC)
The IETF is tackling the security of certain information that is provided by the Domain Name System (DNS) through the release of a number of specifications under the banner DNSSEC. A Hardware Security Module can be used to store and manage the digital keys that are used to sign the artefacts covered within DNSSEC.
Emerging Trends
In recent years, in common with many IT systems, there has been an increase in cloud based HSM infrastructure and solutions. Typically, these augment existing on-premise solutions rather than replace them; as cloud based HSMs offer a limited functional subset of their physical counterparts.
Bring Your Own Key – The process of importing a key generated outside platforms such as AWS or Azure is generally referred to as Bring Your Own Key (BYOK), solutions using this process therefore enable HSM-originated keys to be used in the public cloud.
KT Secure can provide consultancy, training and support for integrating existing HSM infrastructure for these and other emerging technologies and industry drivers in a wide variety of scenarios.
Need help with your HSM?
KT Secure have extensive experience using and managing Hardware Security Modules. Whether you are looking for advice on how to use a HSM in your PKI infrastructure, offload your cryptographic operations to a HSM or looking for someone to deploy and manage your HSMs we can help. Look here for more information about our HSM service offerings.
Although it may seem counter intuitive as to why an organisation may want to outsource the management of its HSMs to a third party – there are numerous business benefits:
- Staff costs saved on both initial training and on-going certifications
- Allows key Staff to focus on less admin related tasks and focus on higher end business processes
- Utilising external supplier may provide more rapid deployment and business agility than internal resources
- Ability to leverage external experience in best practices, process definitions and documentation support
- Reduces vendor or solution tie in by utilising external expertise
